This is how the NSA gets unrestricted access to your iPhone
A new batch of documents suggests the government's spies can remotely turn on your phone's camera and microphone

A free daily email with the biggest news stories of the day – and the best features from TheWeek.com
You are now subscribed
Your newsletter sign-up was successful
The National Security Agency has already demonstrated that it is willing to go to great lengths to swipe information from unsuspecting targets, from bulk-tapping phone records to more absurd stuff like monitoring potential threats in World of Warcraft.
The latest revelations, however, paint an increasingly troubling portrait of the NSA's surveillance capabilities, particularly if you're an iPhone owner. Back in September, German newsmagazine Der Spiegel reported that the NSA had gained access to BlackBerrys, Androids, and iPhones. And now we have a better idea of how backdoor access is unlocked.
According to security researcher Jacob Appelbaum, a new batch of leaked documents showcases how the NSA is able to easily break into iPhones, allowing the agency to gather SMS messages, contact lists, location data, photos, videos, and more. The NSA can even reportedly activate your camera and microphone remotely.
The Week
Escape your echo chamber. Get the facts behind the news, plus analysis from multiple perspectives.

Sign up for The Week's Free Newsletters
From our morning news briefing to a weekly Good News Newsletter, get the best of The Week delivered directly to your inbox.
From our morning news briefing to a weekly Good News Newsletter, get the best of The Week delivered directly to your inbox.
This is accomplished by installing spyware directly onto the device, part of a program called DROPOUTJEEP. Disturbingly, the program reportedly has a 100 percent success rate.
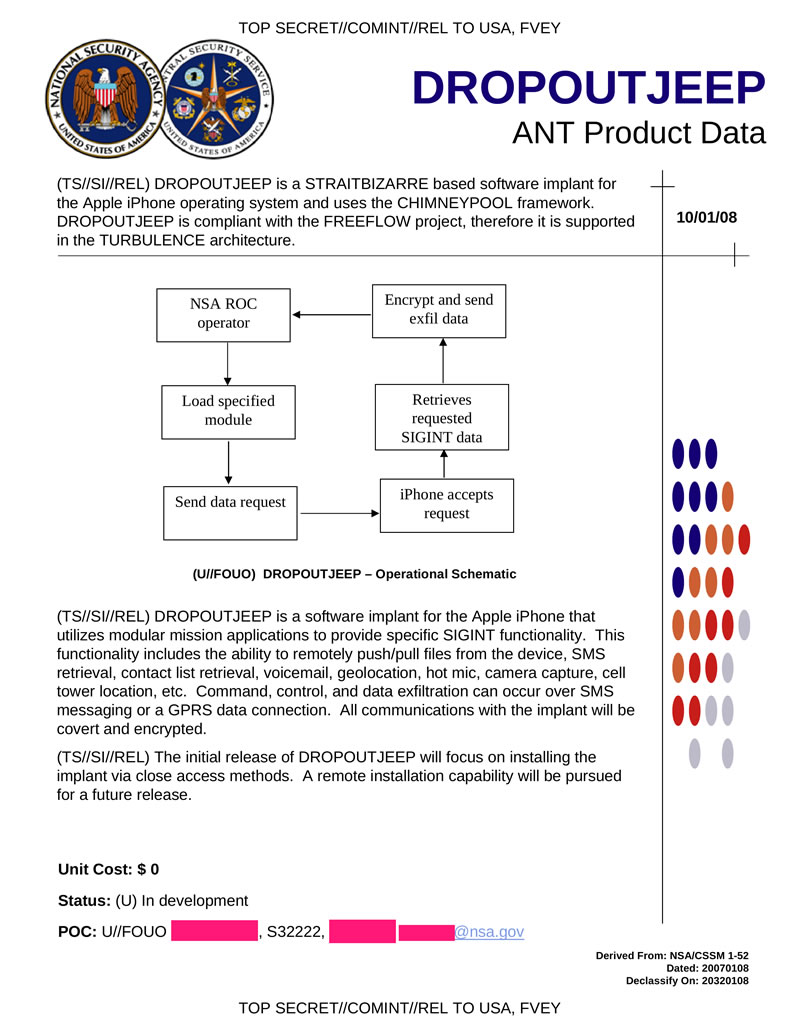
As the Daily Dot points out, it appears that the NSA requires physical access to an iPhone to install the malware, which could be accomplished by rerouting shipments of devices purchased online. Appelbaum presented his findings at the Chaos Communication Conference in Hamburg, Germany, earlier this week. You can watch his talk in full here:
"Either [the NSA has] a huge collection of exploits that work against Apple products, meaning they are hoarding information about critical systems that American companies produce, and sabotaging them," Appelbaum says at one point, "or Apple sabotaged it themselves."
Whether Apple is complicit in the program has yet to be proven. It should be noted that the NSA's very talented super spies seem to get a kick out of exploiting loopholes at big tech companies.
A free daily email with the biggest news stories of the day – and the best features from TheWeek.com
-
 The ‘ravenous’ demand for Cornish minerals
The ‘ravenous’ demand for Cornish mineralsUnder the Radar Growing need for critical minerals to power tech has intensified ‘appetite’ for lithium, which could be a ‘huge boon’ for local economy
-
 Why are election experts taking Trump’s midterm threats seriously?
Why are election experts taking Trump’s midterm threats seriously?IN THE SPOTLIGHT As the president muses about polling place deployments and a centralized electoral system aimed at one-party control, lawmakers are taking this administration at its word
-
 ‘Restaurateurs have become millionaires’
‘Restaurateurs have become millionaires’Instant Opinion Opinion, comment and editorials of the day