An everyman's guide for going invisible on the internet
Protect your privacy with these services

A free daily email with the biggest news stories of the day – and the best features from TheWeek.com
You are now subscribed
Your newsletter sign-up was successful
Let's get this out of the way first: It's impossible to go 100 percent invisible online if you use the internet in any capacity. We still don't completely understand the scope and power of the NSA's surveillance capabilities, and it's highly unlikely that any single individual, no matter how resilient their encryption protocols, could withstand a rigorous investigation by the U.S. government. Still, there are ways ordinary users can better protect their privacy online. This isn't by any means an exhaustive guide; rather, it's a starting point to help educate beginners about the sheer amount of data we leave out there, and what we can do to keep it safe from prying eyes (the NSA's or otherwise).
As always, we also welcome any and all suggestions for going invisible online in the comments below. Here, in no particular order, are a few suggestions:
Use Tor to mask your IP address
The Week
Escape your echo chamber. Get the facts behind the news, plus analysis from multiple perspectives.

Sign up for The Week's Free Newsletters
From our morning news briefing to a weekly Good News Newsletter, get the best of The Week delivered directly to your inbox.
From our morning news briefing to a weekly Good News Newsletter, get the best of The Week delivered directly to your inbox.
Your internet protocol (IP) address is a numerical representation assigned to any device (computers, printers, phones, etc.) that connects to the internet. Outsiders can trace your IP to track who you've been communicating with, what websites you've been visiting, and especially if you've been up to anything illegal, like downloading copyrighted stuff from Piratebay.
That's where Tor comes in. Originally developed by the U.S. Navy, Tor is widely used by activists, hackers, journalists, law enforcement, and many others to evade detection. Basically, it's a system designed to mask your IP address by making its path to the website you want to visit as confusing as possible.
It works by funneling your connection through a series of networked Tor computers at random — like a relay race through a dense crowd of people. Each "relay stop" can only see the IP address of the computer directly before it; by the time you finally connect to your destination, your data path should be split among multiple computers around the world. The more users there are on the Tor network, the harder you are to find.
The easiest way to use it is to download the Tor browser. MIT Technology Review also has a great explainer of how the technology works here.
A free daily email with the biggest news stories of the day – and the best features from TheWeek.com
If you'd rather stick with Chrome or Firefox as your primary browser, you can download the HTTPS Everywhere extension, which encrypts your connection with major websites to make browsing more secure. While the extension project is a collaboration between The Tor Project and the Electronic Frontier Foundation, it's not quite as sophisticated as Tor itself. One big downside: Many sites offer limited support for HTTPS, so browsing can be a bit unpredictable.
Consider setting up a VPN
Virtual Private Networks more-or-less hide your data from the public domain. VPNs were originally set up to allow remote employees access the company's secure servers through encrypted tunnels. But average users can set-up their own VPNs to keep their traffic secure, especially when using something like Starbucks' free WiFi (which crooks can use to glean your password).
You can find plenty of free VPN services out there. One we like is called Hamachi, which is a free tool that allows users to route traffic back through their home internet connection when they're out on the road. It's easy to set up, too.
Another VPN service worth checking out is a one-flick app called TunnelBear, which The Next Web recommends. It's also free though you'll have to pay a $5 fee if you surpass 1GB in monthly data. Not only is it neat-looking (its mascot is a bear!), but it also has apps for both iOS and Android.
Encrypt your sensitive emails
Why should you, a non-whistleblowing, non-spy, encrypt your email messages? Well, if you're sending sensitive information — like social security numbers or bank account information for a wireless transfer — you obviously don't want that kind of stuff to get intercepted by the wrong eyes.
You can encrypt your important emails in a few ways. PC World has a great walkthrough that helps you manually encrypt three different things to ensure maximum security: (1) The connection to your email provider, (2) the actual emails themselves, and (3) the archived and cached versions of your emails.
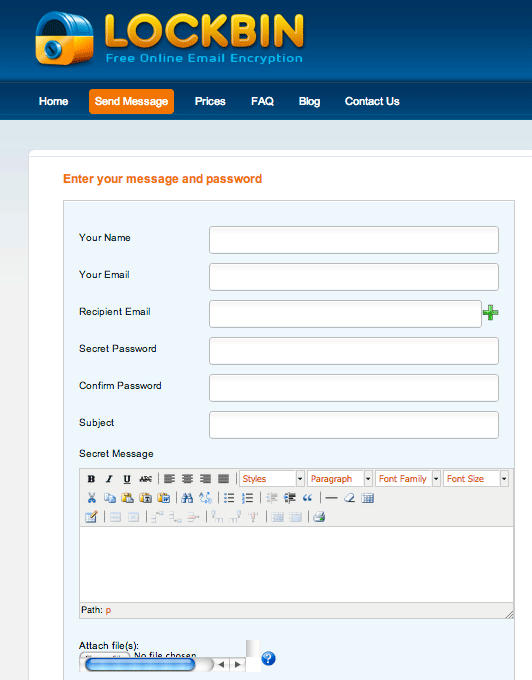
One service we really like is called Lockbin, which promises to protect messages using FIPS 140-2 encryption libraries. Better yet: It's free, and you don't have to register to use it. You just fill out a form with your message and seal it shut with a secret password:
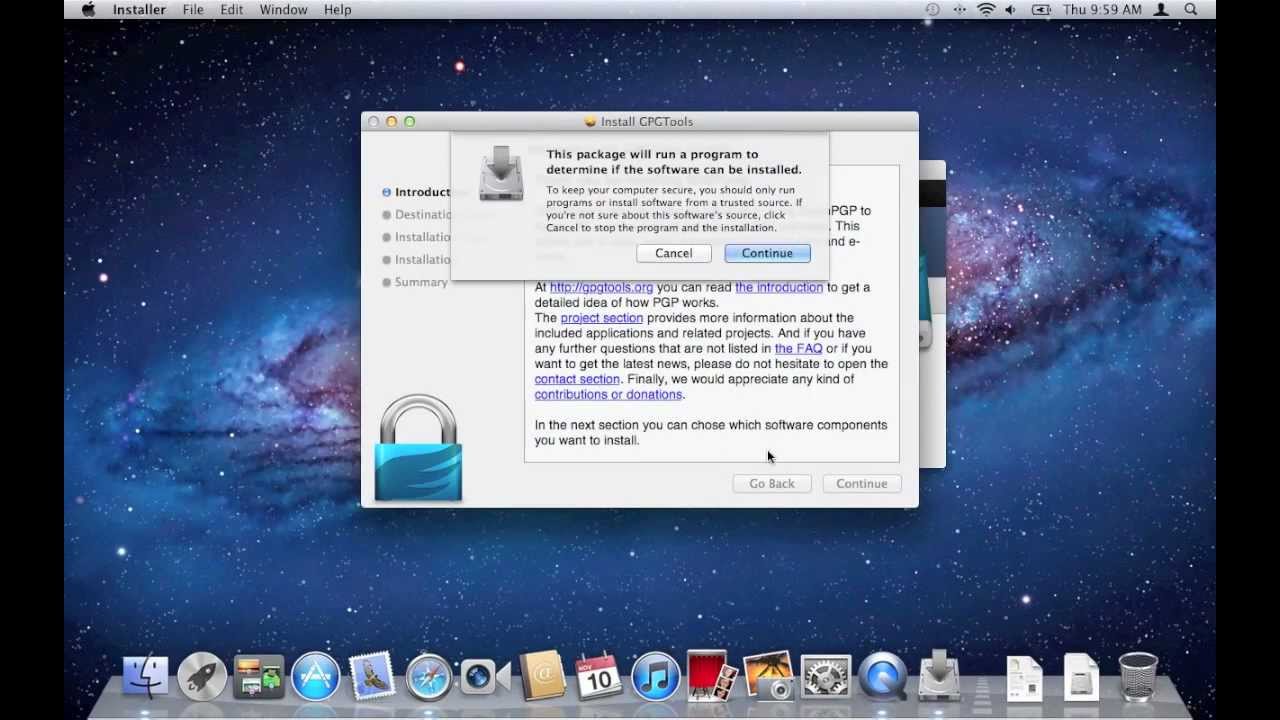
If you're a Mac user, GPG Mail is a free service that generates a PGP (Pretty Good Privacy) key to encrypt your messages. Here's how it looks in action, but you can try it out for yourself here. (Also, if you're interested in learning more about PGP communication, this is a good place to start.)
Don't Google
If you've been following the NSA tracking story, you'll know that Google, Yahoo, and Microsoft (which owns Bing) were all reportedly sending data to the government. (An accusation they have all denied, of course.) If you don't want your search history recorded, try DuckDuckGo, which promises not to track or store your searches. (Although it does use your searches to improve its algorithms.) The service's traffic has increased 50 percent since news of the PRISM program leaked.

Chat in private
Gchat, iMessage, and their ilk are eminently snoopable. If you want to have a real private conversation online, Quinn Norton at ProPublica recommends an encrypted chat service like Cryptocat. To use it, simply download the browser plugin, create a name and a chatroom, and invite whoever you'd like to talk to. As Norton notes, Cryptocat "is hands-down the easiest way to get started with end-to-end encryption, where only you and the person you're talking to can see the message."
Use this guide as a starting point, but let us know below if there are other good services you use to keep your data safe and secure.
-
 Political cartoons for February 21
Political cartoons for February 21Cartoons Saturday’s political cartoons include consequences, secrets, and more
-
 Crisis in Cuba: a ‘golden opportunity’ for Washington?
Crisis in Cuba: a ‘golden opportunity’ for Washington?Talking Point The Trump administration is applying the pressure, and with Latin America swinging to the right, Havana is becoming more ‘politically isolated’
-
 5 thoroughly redacted cartoons about Pam Bondi protecting predators
5 thoroughly redacted cartoons about Pam Bondi protecting predatorsCartoons Artists take on the real victim, types of protection, and more