Why Britain is struggling to stop the ransomware cyberattacks
New business models have greatly lowered barriers to entry for criminal hackers

A free daily email with the biggest news stories of the day – and the best features from TheWeek.com
You are now subscribed
Your newsletter sign-up was successful
On 31 August, Jaguar Land Rover (JLR) noticed an attack on its computer systems. JLR – which employs 32,800 people and supports another 104,000 jobs through its supply chain, mostly in the West Midlands – had to close its factories for over a month. It is estimated that the attack will cost some £1.9 billion. JLR is only the latest victim in a string of ransomware attacks. In the UK alone, Marks & Spencer, the Co-op Group, Harrods, Heathrow Airport, Transport for London and the British Library have all had their operations disrupted in the past two years.
According to GCHQ’s National Cyber Security Centre, “highly significant” attacks rose by 50% in the past year, with 18 incidents affecting the Government, essential services, the economy or a large number of people.
Why is this happening?
Because we’ve built a world that is entirely dependent on a set of technologies which are intrinsically insecure and ultra-complex, and which few people understand. The internet is designed to be easy to access, which of course makes it vulnerable; it suffered its first big hack attack in 1988, when few people had even heard of it.
The Week
Escape your echo chamber. Get the facts behind the news, plus analysis from multiple perspectives.

Sign up for The Week's Free Newsletters
From our morning news briefing to a weekly Good News Newsletter, get the best of The Week delivered directly to your inbox.
From our morning news briefing to a weekly Good News Newsletter, get the best of The Week delivered directly to your inbox.
The more that organisations rely on networked computer technology, the more they’re vulnerable to attack and extortion. Manufacturing and logistics, such as JLR’s, grind to a halt when the systems go down. Hospitals, law firms and other institutions where privacy is paramount can be threatened with data leaks.
How do these hacks work?
There are various ways of invading or disabling a network. Hackers can gain access directly via software vulnerabilities; they can hack lots of unprotected computers and use them as a sort of zombie army, known as a “botnet”, to overwhelm a network.
At present, we are seeing a spate of ransomware attacks. The first step is to get into a network, usually by impersonating an employee. This often involves “phishing” emails, or other inventive forms of manipulation known as “social engineering”: in 2023, hackers combed LinkedIn for MGM Resorts employees with high-level system access, then called an MGM helpdesk posing as one of them and asked for a password reset, which got them in. Once inside, they extend their access, steal sensitive data for extortion purposes and, where they can, take control.
A favoured current target is the “hypervisor”, a server computer that allows many remote machines to use one system (as when employees work from home). Then they use ransomware to encrypt its data, rendering the whole system unusable and making it impossible to recover without paying the hackers for a decryption key.
A free daily email with the biggest news stories of the day – and the best features from TheWeek.com
Why has the problem got worse?
One reason is the huge growth in cryptocurrencies, which make money safer to receive and launder – a record $1.1 billion is thought to have been paid out globally in 2023. They also make it easier to buy illegal services on the dark web. The presence of groups offering “ransomware as a service” (RaaS) – currently the most popular business model – have greatly lowered barriers to entry for criminal hackers.
What is ransomware as a service?
RaaS groups – which advertise on the dark web, with names such as Hive, DarkSide, REvil and LockBit – sell tech support services for ransomware attacks. For a monthly subscription, or a share of the take, they’ll provide encryption software, a payment portal and a dedicated leak site for threatening the victim further, as well as help with the negotiations.
Some are picky about who they’ll hack; LockBit apologised and offered free decryption when one of its affiliates attacked a children’s hospital in Toronto in 2022. This may only be good business sense. DarkSide collapsed as a brand because of the law-enforcement attention it attracted by hacking the Colonial Pipeline, which supplies the east coast of the US with 45% of its fuel, in 2021.
Who are the hacking groups?
The perpetrators range from loose-knit bands of individuals to professionally structured illegal businesses. In the past, many have been in the former Soviet Union and eastern Europe. A Russian-speaking group known as Wizard Spider paid its employees salaries and commission; Evil Corp, another Russian hacking group, offered holiday pay, sick leave and more. Some groups have documented ties to Russian security services; Iran and North Korea appear to sponsor others.
But most cybercriminals are motivated by profit, and can come from almost anywhere. Many of the recent attacks on UK companies – including the Co-op, M&S and JLR – have been traced to, or claimed by, a loose, English-speaking group known as Scattered Spider or Scattered Lapsus$ Hunters. They are known for their exploitation of human vulnerabilities, and for their stunning speed in taking over a network once they have invaded it.
Why can’t they be stopped?
Hackers pose all sorts of problems for law enforcement. Groups are often based abroad in uncooperative jurisdictions, though pressure can be applied: four days after an angry call from Joe Biden to Vladimir Putin in 2021, REvil vanished. Even if based at home, though, groups usually have decentralised, evolving structures that make them difficult to track and stop. Members operate under aliases, using software to disguise their location.
The best way to deter such attacks is through boring but essential measures: installing software security updates; using multi-factor authentication for signing in. The National Cyber Security Centre thinks most ransomware victims aren’t specifically targeted; they just had a vulnerability that was noticed by hackers in a bulk search. Cyber-insurance now seems a necessity. Some smaller companies, like the Kettering haulage group KNP, have had to close because of hacks.
What is ‘Scattered Spider’
Many recent ransomware attacks are the work of closely linked, overlapping groups known variously as Scattered Spider, Scattered Lapsus$ Hunters and ShinyHunters, among other names. They stem from a large underground network that calls itself “The Community” or “The Com”, based largely in the US, the UK and Canada. Many members came into contact with each other as gamers, playing online games such as Minecraft, particularly among “griefing” circles. Griefers deliberately disrupt and “troll” other players. Members of The Com then graduated to cybercrimes: such as cryptocurrency theft and online grooming.
The security company Darktrace describes Scattered Lapsus$ Hunters as “English-speaking, aged 16 to 21, and a little bit neurodiverse”. Paul Foster of the National Crime Agency thinks “Covid probably accelerated their development: more time online, more time on devices”.
The groups plan their attacks through invite-only groups on Telegram, an encrypted messaging service, and other sites. Their British and US accents make it easier for them to fool IT helpdesks. Law enforcement can eventually catch up with them: a series of men in their teens and early 20s, from Florida to Walsall, London to Las Vegas, have been arrested.
-
 How the FCC’s ‘equal time’ rule works
How the FCC’s ‘equal time’ rule worksIn the Spotlight The law is at the heart of the Colbert-CBS conflict
-
 What is the endgame in the DHS shutdown?
What is the endgame in the DHS shutdown?Today’s Big Question Democrats want to rein in ICE’s immigration crackdown
-
 ‘Poor time management isn’t just an inconvenience’
‘Poor time management isn’t just an inconvenience’Instant Opinion Opinion, comment and editorials of the day
-
 Moltbook: The AI-only social network
Moltbook: The AI-only social networkFeature Bots interact on Moltbook like humans use Reddit
-
 Are AI bots conspiring against us?
Are AI bots conspiring against us?Talking Point Moltbook, the AI social network where humans are banned, may be the tip of the iceberg
-
 Silicon Valley: Worker activism makes a comeback
Silicon Valley: Worker activism makes a comebackFeature The ICE shootings in Minneapolis horrified big tech workers
-
 AI: Dr. ChatGPT will see you now
AI: Dr. ChatGPT will see you nowFeature AI can take notes—and give advice
-
 Metaverse: Zuckerberg quits his virtual obsession
Metaverse: Zuckerberg quits his virtual obsessionFeature The tech mogul’s vision for virtual worlds inhabited by millions of users was clearly a flop
-
 The robot revolution
The robot revolutionFeature Advances in tech and AI are producing android machine workers. What will that mean for humans?
-
 Texts from a scammer
Texts from a scammerFeature If you get a puzzling text message from a stranger, you may be the target of ‘pig butchering.’
-
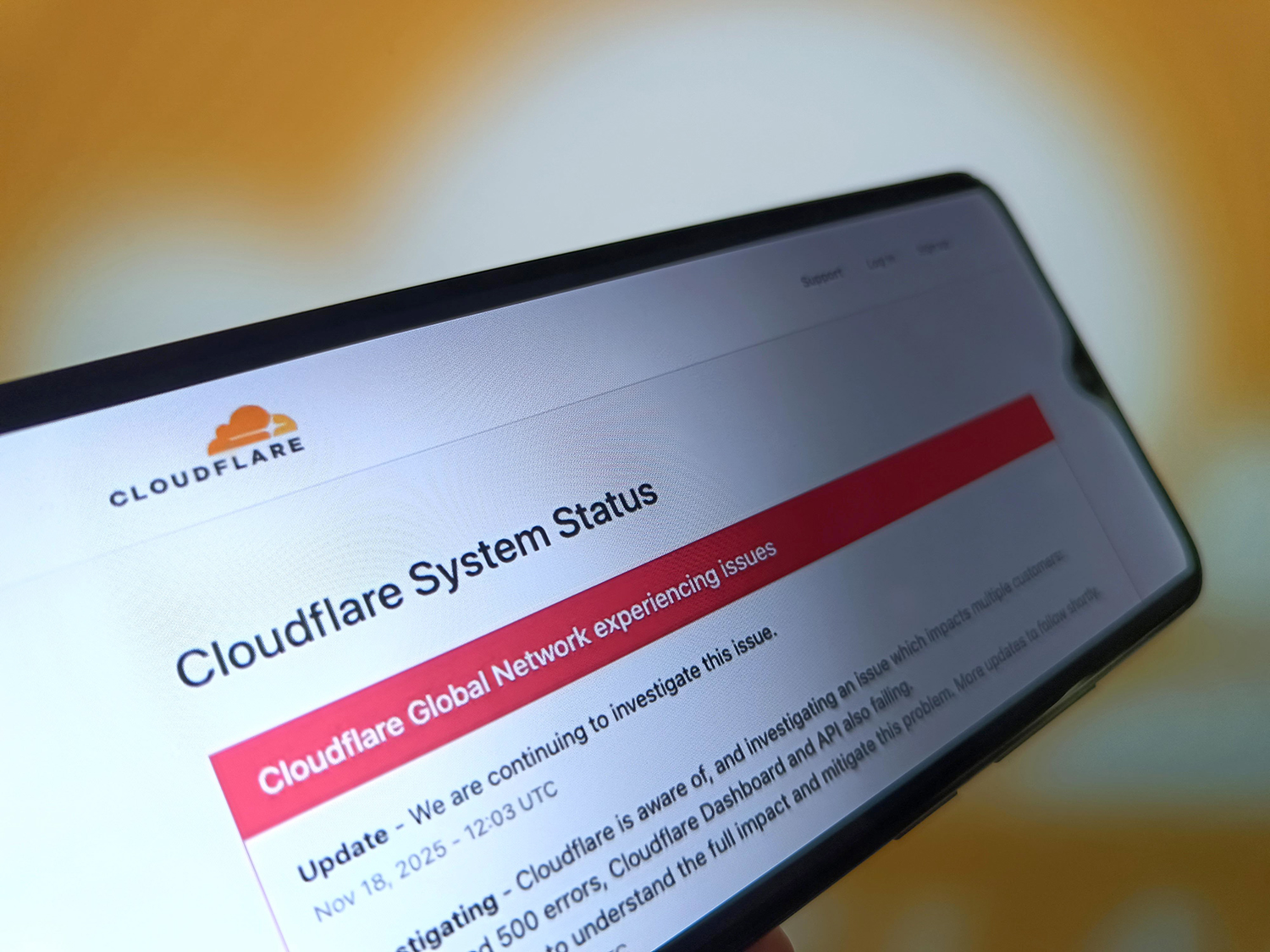 Blackouts: Why the internet keeps breaking
Blackouts: Why the internet keeps breakingfeature Cloudflare was the latest in a string of outages