The cyber debate goes public
Surprise: The NSA's chief is leading the way


A free daily email with the biggest news stories of the day – and the best features from TheWeek.com
You are now subscribed
Your newsletter sign-up was successful
In the parlance of the government, the powerful Gen. Keith Alexander is a "dual-hat."
As director of the National Security Agency, which collects intelligence and keeps and breaks codes, he must operate under the rules of Title 50 of the U.S. code. As the head of the United States Cyber Command (USCYBERCOM), he simply puts on a different hat: Title 10 of the U.S. code, which proscribes conduct for military operations, is his guide.
This germ of a lesson in bureaucratic descriptionaring is a lot more important than it might seem. Alexander is the nation's chief defender of cyberspace, its chief collector of information about cyber threats, and its chief wager of cyberwarfare.
The Week
Escape your echo chamber. Get the facts behind the news, plus analysis from multiple perspectives.

Sign up for The Week's Free Newsletters
From our morning news briefing to a weekly Good News Newsletter, get the best of The Week delivered directly to your inbox.
From our morning news briefing to a weekly Good News Newsletter, get the best of The Week delivered directly to your inbox.
Consider a recent report that Chinese hackers had compromised the White House Military Office's communications systems. WHMO secures communications for the president, runs continuity of government programs, and ensures the integrity of the chain of authorities that allow human beings to launch nuclear weapons. The report alleged that the nuclear command and control (NC2) systems themselves had been compromised; that's not true. WHMO's unclassified email network was hacked; the NC2 systems haven't been touched. But let's say that somehow, China, or someone else, did manage to hack into one of the systems that transmits Emergency Action Messages to, say, strategic nuclear submarines, and a spoof message is somehow transmitted. The U.S. considers any breach of these systems to be an act of war.
Under authorities granted to him by Congress last year, Alexander "has the capability, and upon direction by the president may conduct offensive operations in cyberspace to defend our Nation, Allies, and interests, subject to — (1) the policy principles and legal regimes that the Department follows for kinetic capabilities, including the law of armed conflict; and (2) the War Powers Resolution (50 U.S.C. 1541 et seq.)." That ought to make you gulp a bit.
"Offensive cyberspace operations" to "defend our Nation, Allies, and interests" covers quite a large territory. Is there anything remotely national-security-ish that isn't permitted by that language?
What Americans know about cyberwarfare is unclear. We read about efforts to hack into military systems; we read about intelligence operations meant to sabotage Iranian centrifuges (a clear national security priority if there was one). More prosaically, many of us are the victim of a minor cyber crimes; not a war, per se; but most of us can get our credit problems made whole or our money back. We read a lot about large breaches of privacy, some of them even state-sponsored. (Google informed me and some other journalists and national security experts that China — a "state sponsor," it said — was trying to break into our email accounts. Hand-wringers in the government worry that, short of a major "kinetic," i.e., death-causing cyber incident, citizens are content to live with this "death by a thousand cuts" approach. The pain of cyber crime is just too distributed for most of us to care, or to alter our cyber hygiene, or to demand that the companies we patronize do the same. This is one reason why cyber legislation stalled in Congress last year, whatever it merits. There just wasn't enough public pressure, or interest, to move it along, despite the herculean lobbying efforts of some of the most powerful forces in government.
A free daily email with the biggest news stories of the day – and the best features from TheWeek.com
One major reason why the public doesn't talk a lot about the way our country might engage an enemy in the cyber is this tangle of Title 10/Title 50 authorities and all the equities that secret-keepers have in keeping the rules fuzzy and flexible. That is why it is significant when Gen. Alexander and others agree to talk about cyberwar in public, and especially when they agree to talk about talking about cyberwar.
Consider Alexander's last few months. There hasn't been a single major think tank whose cyber crime panel he has not graced. There he was, in July, talking about cyber threats at the American Enterprise Institute. Later that month, he was in the rarefied air at Aspen, telling a security forum that American cyber defenses were about a "3" on a scale of 1 to 10. Alexander spoke to hacker conventions in August. This week alone, he's at the Woodrow Wilson Center and the U.S. Chamber of Commerce.
Because of Congress's inability to pass modern cyber legislation, the White House will soon issue an order spelling out what authority the executive branch claims in the cyber realm. Reportedly, it will contain the rudiments of an information-sharing procedure for the government and the private sector, and will direct the Department of Homeland Security to design a semi-voluntary system for private companies that do business with critical infrastructure. Already, the Department of Defense requires contractors who do critical work to meet top standards.
The issues Alexander brings up are difficult, and attempts to summarize the sides in this complex debate are inevitably going to be glib. But here's a cheer to Alexander for his commitment to talking about the threat. If the director of the NSA wants to lead the way, by all means, let him. It's up to everyone involved, including the private sector, the White House, civil libertarians, and the media, to follow, and to nurture a robust public discussion. Too much is at stake, including money, privacy, and even the integrity of our laws, to let this subject disappear into the ether.
(Note: I do some work for Palantir Technologies, whose software has attracted the interest of the NSA, according to public reports).
Marc Ambinder is TheWeek.com's editor-at-large. He is the author, with D.B. Grady, of The Command and Deep State: Inside the Government Secrecy Industry. Marc is also a contributing editor for The Atlantic and GQ. Formerly, he served as White House correspondent for National Journal, chief political consultant for CBS News, and politics editor at The Atlantic. Marc is a 2001 graduate of Harvard. He is married to Michael Park, a corporate strategy consultant, and lives in Los Angeles.
-
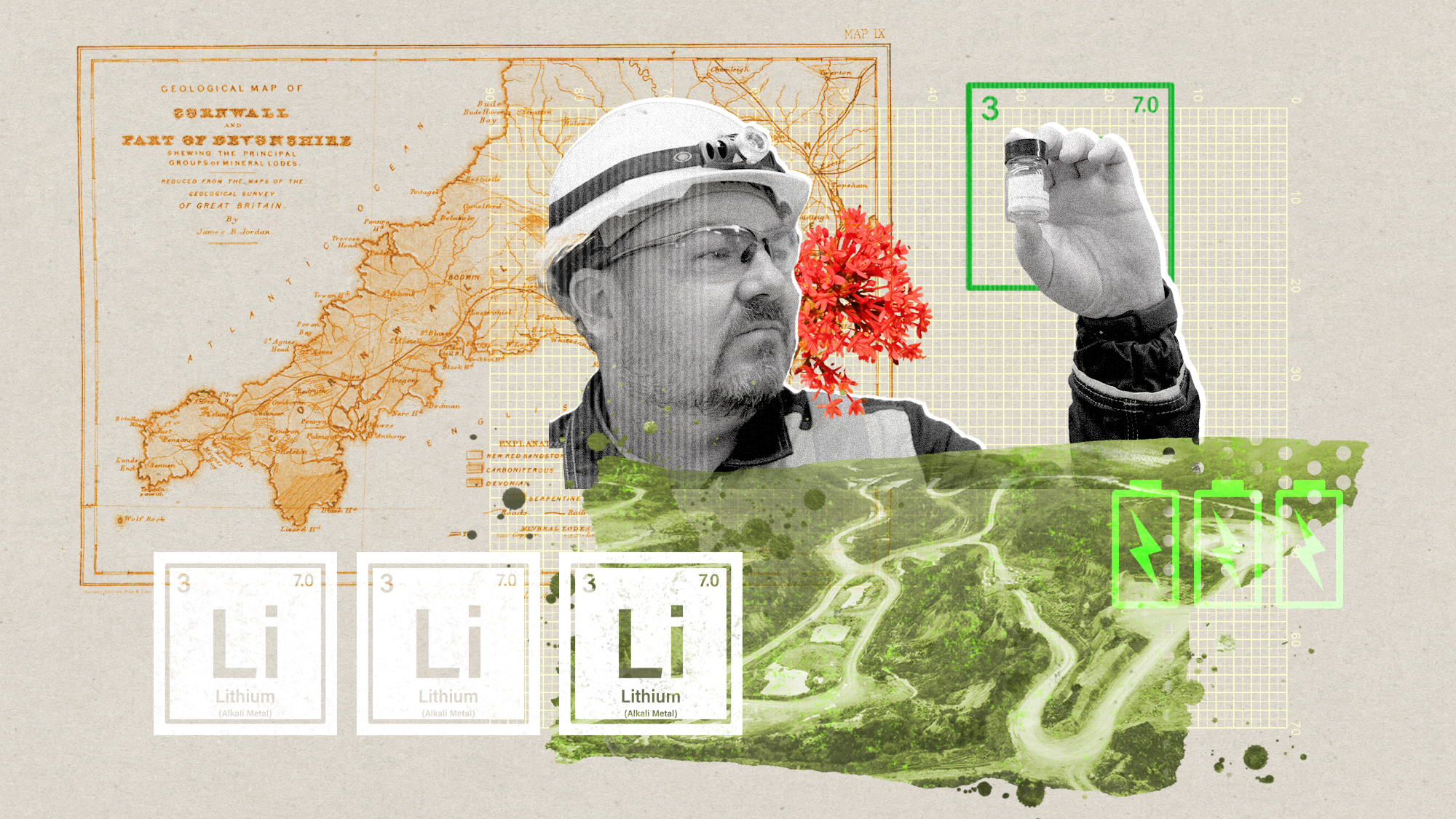 The ‘ravenous’ demand for Cornish minerals
The ‘ravenous’ demand for Cornish mineralsUnder the Radar Growing need for critical minerals to power tech has intensified ‘appetite’ for lithium, which could be a ‘huge boon’ for local economy
-
 Why are election experts taking Trump’s midterm threats seriously?
Why are election experts taking Trump’s midterm threats seriously?IN THE SPOTLIGHT As the president muses about polling place deployments and a centralized electoral system aimed at one-party control, lawmakers are taking this administration at its word
-
 ‘Restaurateurs have become millionaires’
‘Restaurateurs have become millionaires’Instant Opinion Opinion, comment and editorials of the day
-
 Epstein files topple law CEO, roil UK government
Epstein files topple law CEO, roil UK governmentSpeed Read Peter Mandelson, Britain’s former ambassador to the US, is caught up in the scandal
-
 Iran and US prepare to meet after skirmishes
Iran and US prepare to meet after skirmishesSpeed Read The incident comes amid heightened tensions in the Middle East
-
 Israel retrieves final hostage’s body from Gaza
Israel retrieves final hostage’s body from GazaSpeed Read The 24-year-old police officer was killed during the initial Hamas attack
-
 China’s Xi targets top general in growing purge
China’s Xi targets top general in growing purgeSpeed Read Zhang Youxia is being investigated over ‘grave violations’ of the law
-
 Panama and Canada are negotiating over a crucial copper mine
Panama and Canada are negotiating over a crucial copper mineIn the Spotlight Panama is set to make a final decision on the mine this summer
-
 Why Greenland’s natural resources are nearly impossible to mine
Why Greenland’s natural resources are nearly impossible to mineThe Explainer The country’s natural landscape makes the task extremely difficult
-
 Iran cuts internet as protests escalate
Iran cuts internet as protests escalateSpeed Reada Government buildings across the country have been set on fire
-
 US nabs ‘shadow’ tanker claimed by Russia
US nabs ‘shadow’ tanker claimed by RussiaSpeed Read The ship was one of two vessels seized by the US military
