The man responsible for most of your password headaches was wrong, and he's sorry


A free daily email with the biggest news stories of the day – and the best features from TheWeek.com
You are now subscribed
Your newsletter sign-up was successful
In 2003, Bill Burr, a manager at the U.S. National Institute of Standards and Technology, wrote an 8-page paper titled "NIST Special Publication 800-63. Appendix A." That document — which suggested people come up with obscure passwords with capital and lower-case letters plus symbols and change their passwords often — became the cornerstone of corporate password management and internet security conventional wisdom for more than a decade. Now, Burr, 72 and retired, has a confession and an apology, The Wall Street Journal reports. "Much of what I did I now regret," he said.
When he wrote those guidelines, Burr tried to find empirical data to base his recommendations on, but there wasn't any available; he also says he was under pressure to complete his paper quickly. But thanks to years of massive hacks and leaked passwords, researchers can see what kind of passwords people are using, and it turns out, people aren't as clever or original as they think. "Changing Pa55word!1 to Pa55word!2 doesn't keep the hackers at bay," notes the Journal's Robert McMillan.
In June, NIST published a revised version of Burr's document, with much of his advice excised. After expecting to do a light edit, "we ended up starting from scratch," says Paul Grassi, who led the two-year review and rewrite. Now, the best practice is to come up with a long and easy-to-remember password and change it only if there's evidence of a security breach. In a widely shared cartoon, Randall Munroe accurately estimated that a Burr-type password like "Tr0ub4dor&3" could be cracked in three days, while four common words jammed together — "correcthorsebatterystaple" — would take 550 years to crack. You can go change your passwords now, and read more at The Wall Street Journal.
The Week
Escape your echo chamber. Get the facts behind the news, plus analysis from multiple perspectives.

Sign up for The Week's Free Newsletters
From our morning news briefing to a weekly Good News Newsletter, get the best of The Week delivered directly to your inbox.
From our morning news briefing to a weekly Good News Newsletter, get the best of The Week delivered directly to your inbox.
A free daily email with the biggest news stories of the day – and the best features from TheWeek.com
Peter has worked as a news and culture writer and editor at The Week since the site's launch in 2008. He covers politics, world affairs, religion and cultural currents. His journalism career began as a copy editor at a financial newswire and has included editorial positions at The New York Times Magazine, Facts on File, and Oregon State University.
-
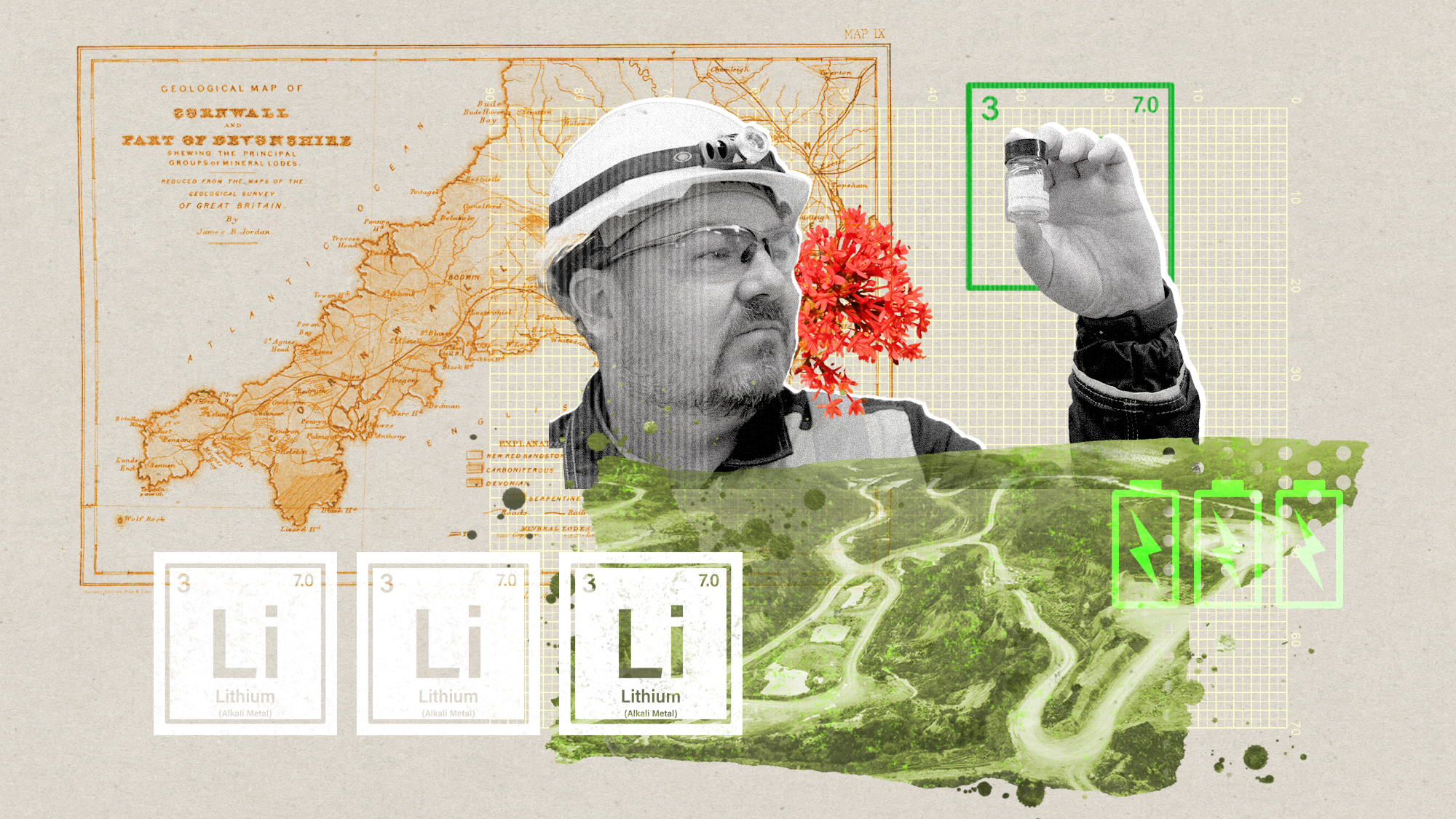 The ‘ravenous’ demand for Cornish minerals
The ‘ravenous’ demand for Cornish mineralsUnder the Radar Growing need for critical minerals to power tech has intensified ‘appetite’ for lithium, which could be a ‘huge boon’ for local economy
-
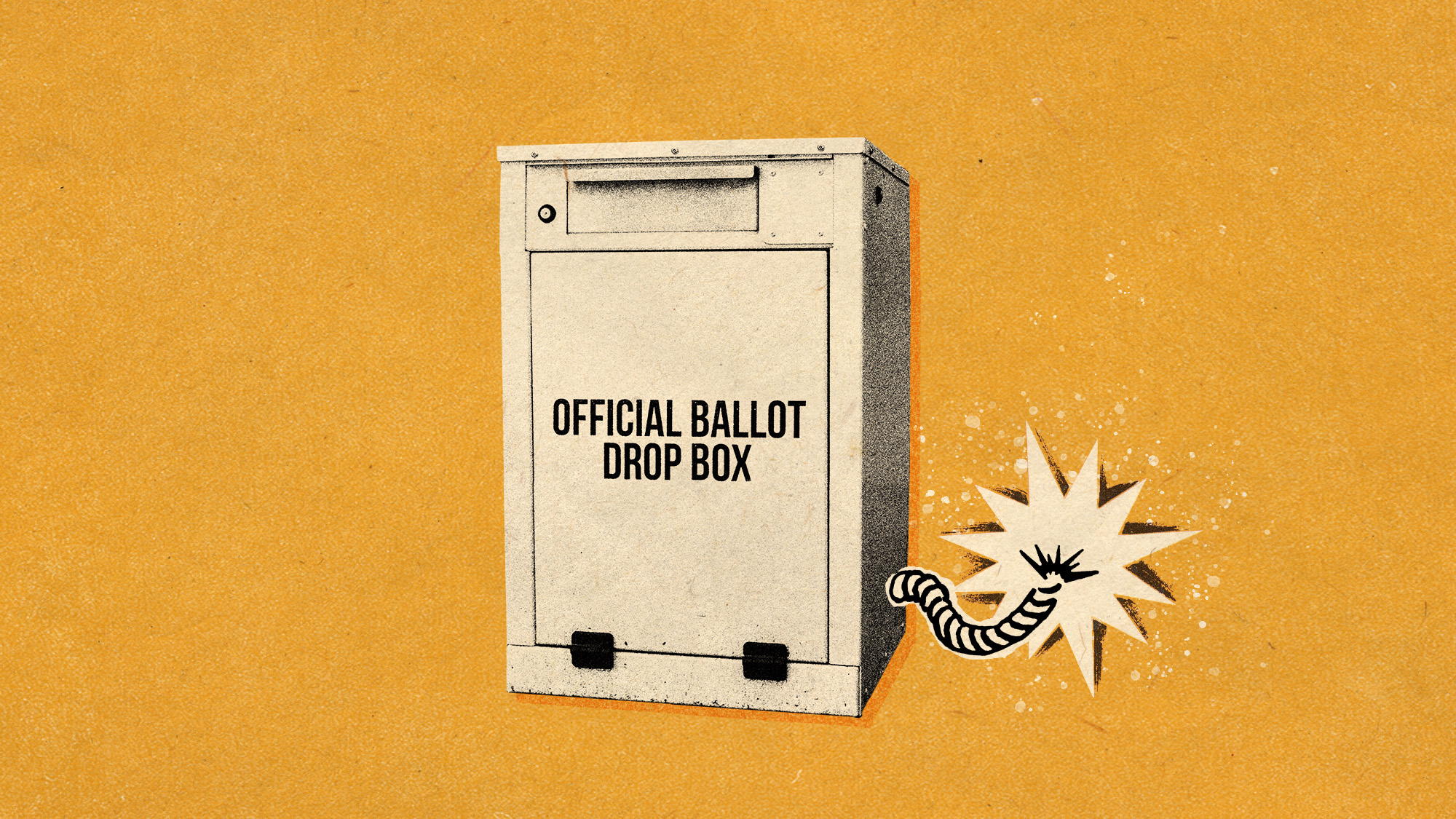 Why are election experts taking Trump’s midterm threats seriously?
Why are election experts taking Trump’s midterm threats seriously?IN THE SPOTLIGHT As the president muses about polling place deployments and a centralized electoral system aimed at one-party control, lawmakers are taking this administration at its word
-
 ‘Restaurateurs have become millionaires’
‘Restaurateurs have become millionaires’Instant Opinion Opinion, comment and editorials of the day
-
 TikTok secures deal to remain in US
TikTok secures deal to remain in USSpeed Read ByteDance will form a US version of the popular video-sharing platform
-
 Unemployment rate ticks up amid fall job losses
Unemployment rate ticks up amid fall job lossesSpeed Read Data released by the Commerce Department indicates ‘one of the weakest American labor markets in years’
-
 US mints final penny after 232-year run
US mints final penny after 232-year runSpeed Read Production of the one-cent coin has ended
-
 Warner Bros. explores sale amid Paramount bids
Warner Bros. explores sale amid Paramount bidsSpeed Read The media giant, home to HBO and DC Studios, has received interest from multiple buying parties
-
 Gold tops $4K per ounce, signaling financial unease
Gold tops $4K per ounce, signaling financial uneaseSpeed Read Investors are worried about President Donald Trump’s trade war
-
 Electronic Arts to go private in record $55B deal
Electronic Arts to go private in record $55B dealspeed read The video game giant is behind ‘The Sims’ and ‘Madden NFL’
-
 New York court tosses Trump's $500M fraud fine
New York court tosses Trump's $500M fraud fineSpeed Read A divided appeals court threw out a hefty penalty against President Trump for fraudulently inflating his wealth
-
 Trump said to seek government stake in Intel
Trump said to seek government stake in IntelSpeed Read The president and Intel CEO Lip-Bu Tan reportedly discussed the proposal at a recent meeting
